|
|
|
Distinguished Toastmaster
BUSINESS & BRANDING COACH . LIFE & LEADERSHIP STRATEGIST MOTIVATIONAL SPEAKER SERVING ENTREPRENEURS & MAIN STREET |
________________________________________________________________________________
CASHING IN ON HEALTHCARE.GOV "CLICKS" (c) Carrie Devorah : ________________________________________________________________________________
The danger of the Healthcare.gov conversation on Capitol Hill are the issues not yet investigated by Legislators, towards determining Healthcare.gov is even more of an online data stealing train wreck waiting to happen. Finger pointing has been over the top by Legislators who signed the Affordable Health Care Act, without waiting to read the ever changing law. The Hill Hearings are not adressing the profiteers of Clicks, flash auctions, yes even spam on the beleaguered website. Healthcare.gov is a tsunami of litigation poised to launch. It wouldn’t be this way, if Legislators had their finger on the pulse of issues addressed in colleagues committee rooms. It doesn’t take much to grasp that Healthcare.gov Users are at risk, down the road, for claims of Patent Infringement, also called Patent Trolling. Patent Trolling is legal remedy being sought for unauthorized use of the Owner’s Copyright, Trademark and/or Patent. Healthcare.gov utilizes all three.
Conversations addressing Internet Users being sued for Unauthorized Use of a Patent, Trademark and/or Copyright are going on- in print, online, in Broadcasts just not in relevant Congressional Hearing Rooms where witnesses called to testify are being asked what went wrong with the rollout of the Affordable Care Act. The question witnesses are not being asked is ‘what went right with the ACA roll out.’
A lot.
Healthcare.gov, the insurance marketplace and Cuidadosesalud.gov, the Spanish health site, are gravy train presenting hidden risk to the site Users, presenting great profit opportunities. Despite news cycles dominated with talk of data capture by the NSA or Consumer Data sold for mobile marketing algorithm development, there is virtually no discussion Healthcare.gov succeeded from its first click without even making one User Insurance policy sale. Healthcare.gov was brilliantly set up for profit .
Its called the business of CLICK. Lead generators and list brokers, in the financial services industry, take in $100 million a year, with their market growing by more than 16 percent annually. Within seconds of ‘landing’ on the Healthcare.gov site, even before they clicked one of the three option buttons top of the site (i) See Plans Before Apply (ii) Apply now for Health Coverage and (iii) Use Your Coverage, visitors are Bought & Sold through Online data auctions wars driven by Robots “Flash bidding” for rights to buy/sell their Identities, for Pop up placements, for sending the Visitor similar product pitches.
Healthcare.gov can be called a “List Broker.” The site has data to sell. Yours.
Take the example of John and Jane Doe and Healthcare.gov . John and Jane Doe fill out their ACA application or leave their email address or “save.” The information John and Jane Doe enter is “tested” against databases of e-mail and home addresses the lead generator already had compiled or bought. Tested is another word for background check using data you did not know the profiteers had compiled. John and Jane Doe’s entered data is being checked, keystroke by keystroke, for authenticity. Once, authenticated, John and Jane Doe’s name and data is flowed into the electronic auction system, “Ping Tree.” Data Buyers have seconds to decide to buy or pass.
The FTC knows about lead generators and list brokers. The FTC, addressing one of these entities at a time, is playing whack-a-mole. The FTC is yet to address shuttering the “model” rather than the individual players. It doesn’t take long before other such sites are put together, taking data gleaned from other sites. Spokeo. Yatedo. 123people.com are on the FTC’s radar now.
Healthcare.gov was modeled for profits not consumers. Similar models that require less personal information to be able to give Consumers “Click-to-Brick-lead,” are the online car insurance industry and other insurance models where minimal Consumer’s personal data is requested.
The Healthcare.gov online Marketplace model is similar to brick-and-mortar payday lender models, except, payday loans are typically secured by a post-dated check. Visitors must provide data on household members and income in order to price shop in the Marketplace. Income data needed to factor MAGI, Modified Adjusted Gross Income, includes, “SSI payments, disability payments, unemployment compensation, wages, salaries, tips, pension income, rental income, investment income, retirement income, prizes, awards and gambling winnings. Child support, gifts SSI, veterans disability payments, workmen’s comp and loan proceeds.”
The “future” of using this model is clear. Consumers using the Financial Industry’s parallel model have complained to Regulators their financial data has been misused or stolen after entering the auction system. The auction system is step one in Data Brokering. The FTC can testify on what the Regulators learned while investigating AMG Service Inc, an Oklahoma tribal entity selling PayDay borrowers data. The FTC learned, while investigating AMG Services In, an Oklahoma tribal entity, that once the User gave their private details, Users accounts can be entered into and withdrawn from without the User’s agreement or knowledge. AMG Services In, an Oklahoma tribal entity was selling PayDay borrowers data.
Senator Jeff Merkley, (D- Oregon) announced he is preparing a bill to outlaw online lead generation. Merkley signed on to the Affordable Health Care Act, including a provision in the 2010 health care reform law ensuring new mothers have “time and space to pump milk at work.” Merkley’s bio says nothing of protecting these moms from List Brokers and Lead Generators. [http://www.merkley.senate.gov/about/biography/ ]
Who are these List Brokers and Lead Generators benefiting from Users being Cookied, Cached, followed and auctioned without even leaving the landing page? Senator Merkley said the Financial Services Industry websites mask the true identities. Merkley has been silent on saying Healthcare.gov unmasks them.
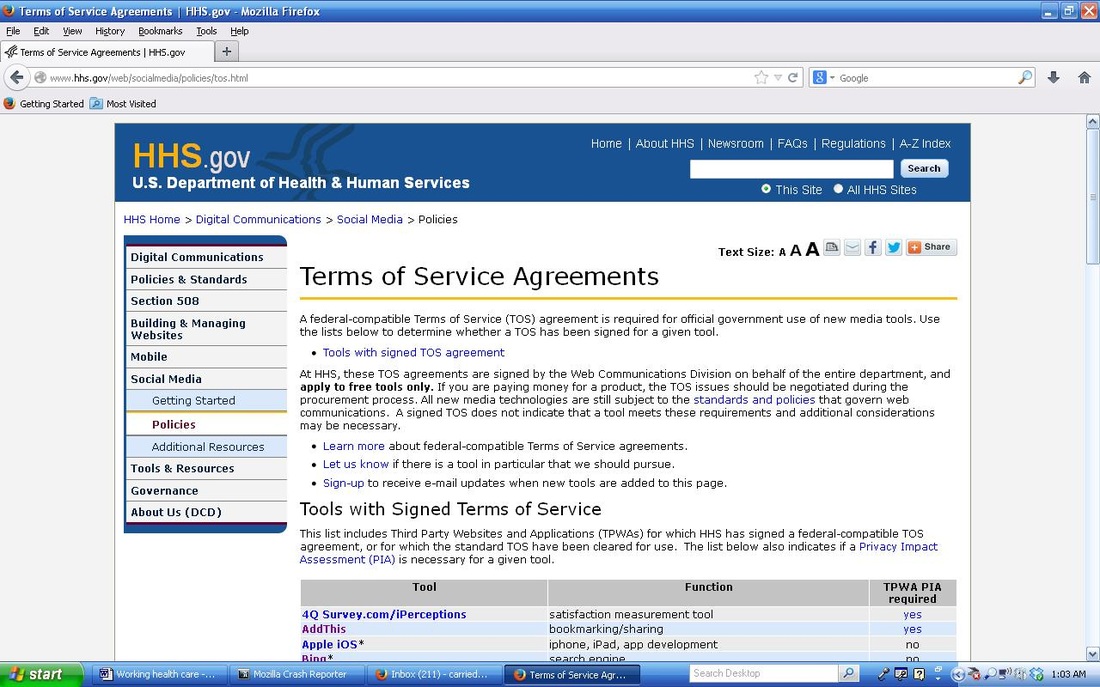
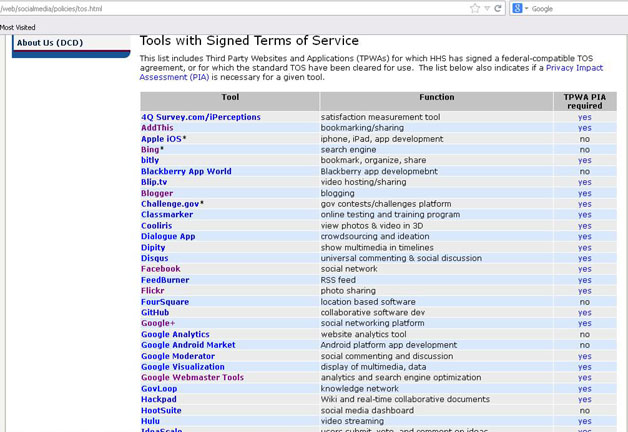
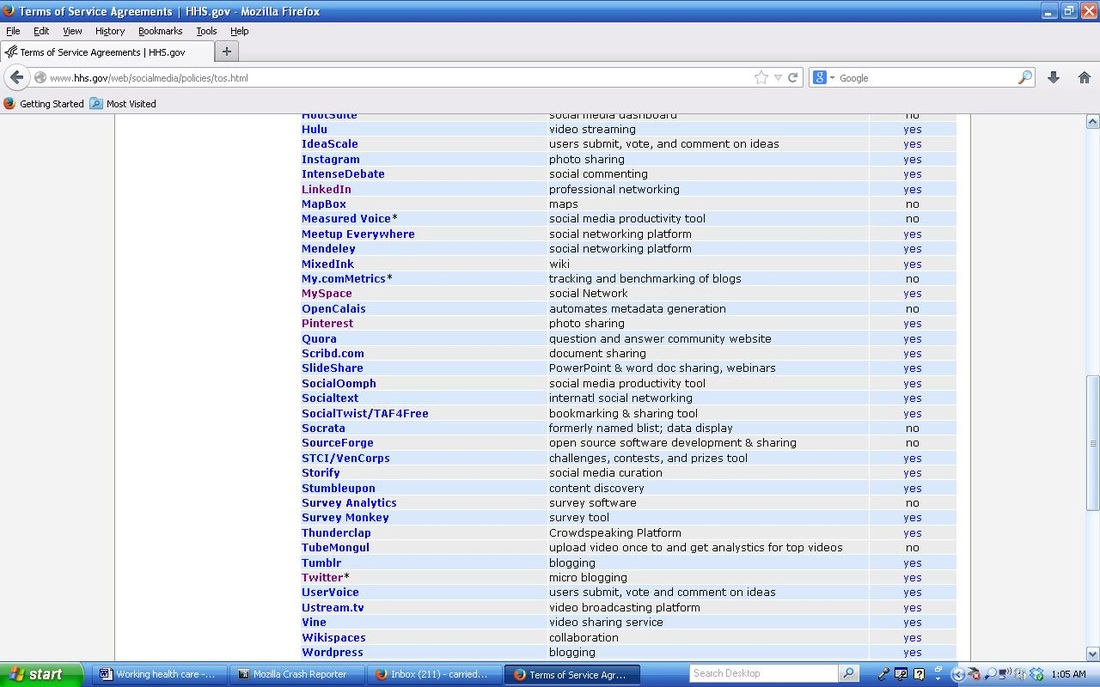
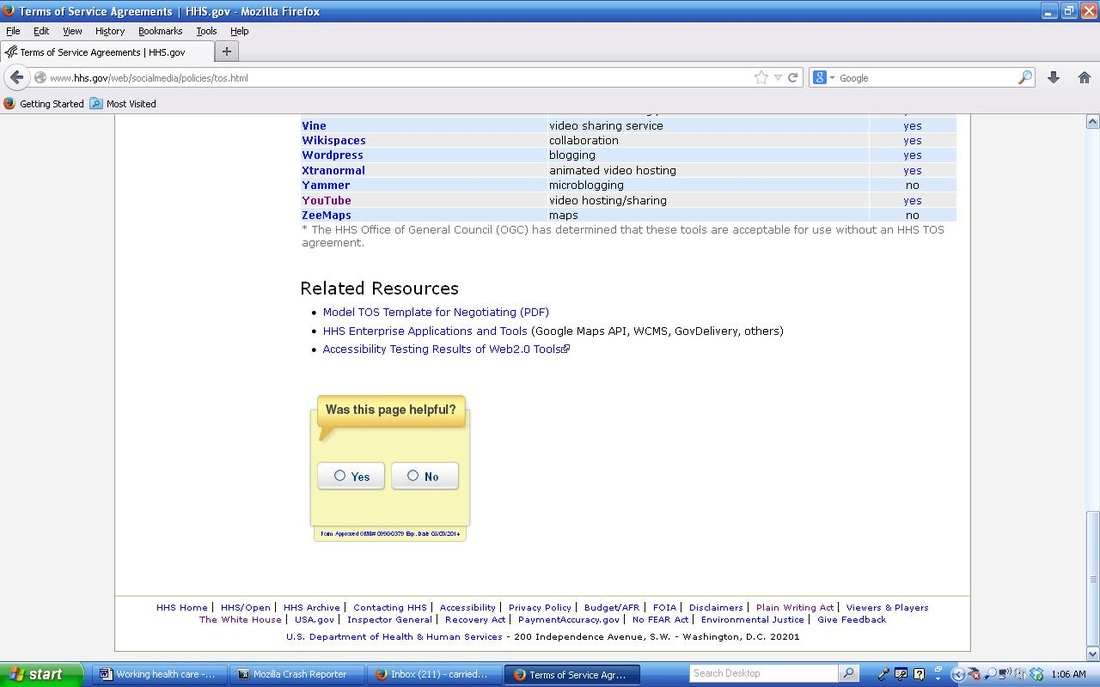
What is known, is “the HHS Office of General Council (OGC) has determined that tools “acceptable for use without an HHS TOS agreement.” This is stated on the Healthcare.gov pages. The provided list of tools includes, but is not limited to STCI, Vencorps, Storify, Stumbleupon, Survey Monkey, Tumblr, Twitter, User Voice, Vine, Wikispaces, wordpress, xtranormal, youtube, flickr, github, google+, google moderator, google visualization, google webmaster tools, govloop, hulu, ideascale, instagram, intensedebate, linkedin, meetup everywhere, mendeley, mixedink, myspace, pinterest (photo sharing), quora, scribd.com, slidehsare, socialoomph, socialtext
Twitter is Asterisked. Measured Voice is asterisked, My.comMetrics is asterisked.
Data bundling is big business, so big that Menlo California Venture Capitol companies like Menlo Ventures [www.menloventures.com ] continue to seed companies with millions of dollars, through various rounds of funding. Some companies “make it.” Others? Well, it’s a numbers game. Seed fast, often and hope big.
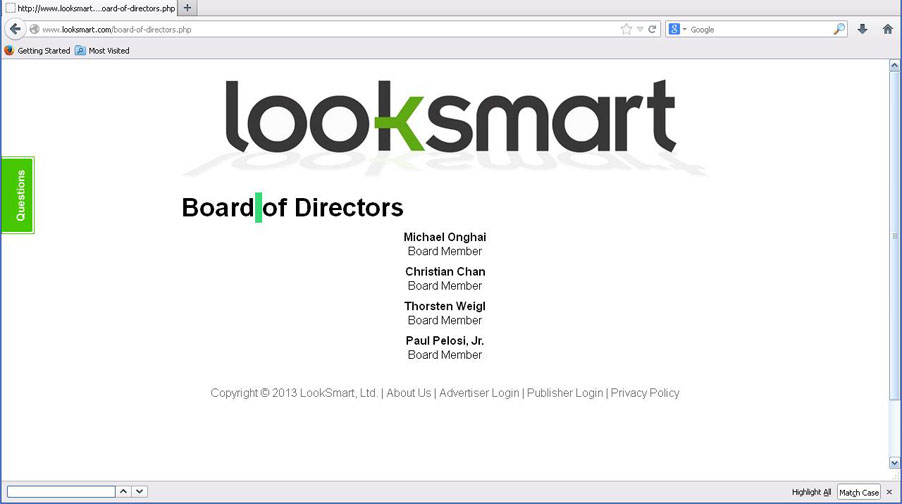
An example of a Data company counting Clicks Data is LOOKSMART Ltd formerly LOOKSMART Holdings Ltd, a Delaware haven state corporation, founded in 1996 in California, #CA1991955. LOOKSmart [ www.looksmart.com ] is just being used as an example of a “Search and display advertising network solution on multiple continents. There is no known connection to the Affordable Health Care Act and Healthcare.gov, at this time, other than blood. Paul Pelosi Jr, an executive of LOOKSmart, according to Businessweek, is the son of former Speaker of the House Nancy Pelosi. Looksmart, based in California, trades on the NASDAQ under the symbol LOOK. In 2012, LOOK’s operations expense was $6 million in the year ending December 2012. LOOKSMART was delisted June 2013. It was trading at 0.76. LOOK trading January 31 2014 at $2.52 - $2.65.
That would be up to Congressional investigators to look in to and determine if and who is profiting from flash auctions, clicks, webcrawlers, list brokering, lead generating and Spam. LOOKSmart is of that genre profiting from sites like Healthcare.gov LOOKSmart does Search Advertising.
LOOKsmart uses its “Adcenter platform technology.” LOOKSmart “provides advertisers the ability to buy graphical display advertising.” “It allows multiple search advertising customers to upload keywords, manage daily budgets….” Etc, and the companies customers include “intermediaries who purchase clicks to sell into the affiliate networks of search engine providers, direct advertisers and their agencies whose objective is to obtain conversions or sales from the clicks and self service advertisers that sing up online and pay by credit cards….”
Like the ACA.
Pelosi Jr. Paul’s knowledge of this industry makes Paul a credible witness to explain to Congress exactly how the business of CLICK works and its impact on Healthcare.gov. Investing/Businessweek profiled LOOKSmart in detail [ http://investing.businessweek.com/research/stocks/snapshot/snapshot.asp?ticker=LOOK ]. “Company Description” states “The company derives the majority of its traffic from its pay-per-click distribution network partners. Each click is verified through its proprietary network traffic monitoring and management process, as well as third party technologies and tools.” It continues “Through a web interface or its proprietary API, the company’s AdCenter allows multiple search advertising customers to upload keywords, manage daily budgets, set rates and view reports, including spending data that is updated hourly. Search advertising customers can also access keyword suggestions, price and traffic estimates, online help and frequently asked questions.” It goes on to explain how AdCenters for Publishers…”integrates dominant third-party feeds, within a single auction based platform for cost-per-click text based advertising and access to a “backfill” of adverisiers so they can ramp their online operations and not lose time or existing revenue sources while establishing their advertiser relationships.”
Concerns for Healthcare.gov Users, doesn’t end there with CLICK worries. It continues. Keyword, “Sources.” Who are they?
The role of Legislators, separated by walks across the Capitol, or an amble around the corner and down the hall, is to get these questions answered. Sometimes that short distance to answers seems almost a plane ride distance cross country away. A couple of hearing rooms away from the Energy and Commerce Committee adressing oversight Of Healthcare.gov with Secretary Sebilius, the Committee on the Judiciary held an Intellectual Property hearing that should send chills up the spine of the Legislators. And Healthcare.gov Users.
This Hearing, adressing Patent Trolls, hear testimony from the Hotelier industry’s General Counsel. The General Counsel testified his Hoteliers constituency are learning the hard lesson of installing onsite WI-FI for keeping their customers’ wired. He said his Hoteliers are being sued for patent infringement by owners whose components areintegrated in to the Technology Tangle that makes WI-FI work. A spokesperson for Wendy’s explained the Internet Of Things is perceived as a “need” in a data driven make-the-consumer-happy culture. Sell through doesn’t necessarily match the expense and cost of maintenance. This isn’t guesswork. The numbers supporting evidence of trending away from IOT, should have factored in to building healthcare.gov.
Maybe it was. Click. Caching. Users are human. Curious. Crave interaction. Believe it or not, all things done, people prefer people in the flesh.
The Judiciary hearing did not bring home the lesson that (i) people don’t read to the bottom of pages where TOS and PRIVACY Clicks are positioned. Websites are tangled Technologies with multiple layers of Terms of Service and Privacy Agreements. Few of these Agreements are seen, let alone read. Fewer of the Terms Of Service are understood by site Users. The Technologies are owned by parties who are proprietary when it comes to Unauthorized use of the IP, Intellectual Property.
Even if someone did read to the page bottom, the likelihood they will read each of the CLICKS from entry to exit, is minimal. If they did? The likelihood they comprehended the ramifications of each Software’s Liabilities on the webpage, is doubtful. These Third Party sites are not bound to the Obama Administration’s “Plain Writing Act.” They should be. TOS stating the legalities Users are written in thousands of words by lawyers, are bound to, but only AFTER, John and Jane Doe hit the sites landing page. There is no warning Pop-Up (they have to click off) before being bound to the site’s consequences and Terms such as being bound to resolve through arbitration, Legal Remedies with a Cap, consequences of violating the TOS and the forum for arbitration may be cross country, for example, in California, not at all close to the Users home. More important, is the TOS they read then, in the Internet world, without notice by the software or app manufacturer, may not be there tomorrow. The Internet World is fickle that way.
Multiply the time it takes to read one software developers TOS by the number of developers software Technology tangles in the Healthcare.gov site and THEN factor in the real fact the New York Times is written for 8th grade reading level, most accomplished people can’t grasp TOS, let alone the Third Party TOS for Healthcare.gov. Jeff Foxworthy has proven few of us are smarter than a 5th grader [ http://www.tvguide.com/tvshows/are-you-smarter-than-a-5th-grader/photos/286397/55291 ]
Legislators are not grasping that Healthcare.gov, managed by the U.S. Centers for Medicare & Medicaid Services. 7500 Security Boulevard, Baltimore, MD 21244, is more than a landing page. [ whois.com indicates internic.net as a related domain name for Healthcare.gov . Internic Whois.com is ICAAN based in Los Angeles, downtown, Waterfront [ http://www.whois.com/whois/internic.net ]
ACA is a website. CMS is a website. HHS is a website. They are linked to each other. They are linked to third party sites. Websites are hacked almost daily. Websites cannot be secured even the websites of the entities that developed the software that was hacked ie. 2013- Adobe Systems, 152 million; Target Corp, 70 million; 2012- Shanghai Roadway D&B, 150 million; 2011- Sony, 77 million; 2009- Heartland Tower Federal 130 million; 2007- TJX, 94 million; 1984- TRW, Sears Roebuck, 90 million.
Ben Simo, past president of the Association for Software testing, discovered Healthcare.gov vulnerabilities. Simo did not set out to discover the ACA security vulnerabilities. Simo just wanted to insure his family. Sino said the ACA site had so much “cookie” tracking data he felt the ACA’s capacity was exceeded. Simo said the email verification system could be bypassed without even accessing his email account. Simo, preferring to call himself a software tester not hacker, said he discovered the ACA site relayed personal information over the Internet without encryption.
Healthcare.gov is covered with links to other pages, sites policies, contact us, viewers, players, even to something called the Plain Writing Act [ www.plainlanguage.gov/howto/guidelines ]. The Plain Writing Act is required of Government entities and employees to write content so Users can understand. Third Party entities linked to Healthcare.gov are not held to the Plain Writing Act standard. Visitors to the site Click away not knowing they are at risk of IP, ID, Commerce Theft and Litigation theft as they travel page to page on Healthcare.gov. This must be pointed out to site Users so they act informed. Enter Healthcare.gov, intended or not, you are giving away data to strangers who can be anywhere in the world and may one day send you a letter just like the Hotelier GC testified his clients are shocked to receive- ‘You Are An Infringer. You Are Being Sued.’
The User’s Data as List Broker or Lead Generator fodder, on the ACA timeline, is not defined. All that is stated is “Healthcare.gov will keep data collected long enough to achieve the specified objective for which they were collected” in that the gathered data falls under the National Archives and Records Administration, NARA, General Records Schedule (GRS) 20-ittem IC, “Electronic Records” handled “according to the requirements of that schedule [ www.archives-gov/records-mgmt/grs20.html ] Long enough is not defined. The question is raised if the gathered data is held in any way by National Archives and Records Administration, NARA.
Page 5 of the printed Privacy Policy advises “how healthcare.gov uses third party websites and applications,” it says, “as a response to OMB Memo M-10-06, Open Government Directive,” using a “variety of technologies and social media services to communicate and interact with citizens… third-party website and application (TPWA) tools” including “popular social networking and media sites, open source software communities and more,” without listing “more.” Examples are given- Facebook, Twitter and youtube. If reading “open source software communities” wasn’t enough to know someone, somewhere potentially knew how to enter the site or had developed a backdoor to the date, then Users, if they read this far, are advised that the “TPWAs are not exclusively operated or controlled by HealthCare.gov. Users of TPWAs often share information with the general pubic, user community and/or the third party operating the website.” “These actors may use this information in a variety of ways.” “TPWAs could cause PII to become available or accessible to healthcare.gov and the public, regardless of whether the information is explicitly asked for or collected by us.”
PII? Personally Identifiable Information.
That the Affordable Care Act, HHS and/or Healthcare.gov may have their agreement to use these Technologies does not mean visitors to ACA are grandfathered in under their agreement. Bluntly, if, as the hoteliers using WI-FI are finding out, is the day one of the Healthcare.gov’s software’s developers determines their IT IP is being used by one or many Users without legal Authority, there is the potential for each and every of the ACA Users to be sued.
Hair brained notion? Not at all.
And if John and Jane Doe decide to post their horrible experience online, their fate may be the same as Jen Palmer who wrote a negative review on Ripoff Report. Jen had not seen, in using a site she ordered product from that she never received, she had in fact agreed, ““this sales contract prohibits you from taking any action that negatively impacts KlearGear.com, its reputation, products, services, management or employees. Should you violate this clause, as determined by Kleargear.com in its sole discretion you will be provided a seventy-two(72) hour opportunity to retract the content in question. If the content remains, in whole or in part, you will be billed $3,500 USD for legal fees and court costs until such complete costs are determined in litigation. Should these charges remain unpaid for 30 calendar days from the billing date, your unpaid invoice will be forwarded to our third party collection firm and will be reported to consumer credit agencies until paid.” The unexpected $3500 bill woke Jen up.
What recourse does Healthcare.gov Users have being groomed and led in to these potential legal risks without advance notice before hitting the site’s landing page?
There are sites Users can go to to “opt out from Online Behaviour of Advertising. Aboutads.com, for one browser, indicated over 118 Participating Companies [ www.aboutads.com ] A note down the Aboutads.com page is important to read. It states “important things to remember about the choices you make on this page: These opt outs apply to interest based advertising by participating companies. You will still receive other types of online advertising from participating companies and the Web sites you visit may still collect information for other purposes.” Among the companies, Google Inc, LiveRamp, LiveRail, exelate, Glam Media and Experian Marketing Services.
HHS.gov presents an empathetic shoulder to its Users. [ Protecting the Public’s Privacy ] “Federal agencies are required to take specific steps to protect individual privacy whenever they use third-party websites and applications to engage with the public. When using a third-party website or application, agencies should adhere to the following requirements: Examine the third party’s privacy policy to evaluate the risks and determine whether the website or application is appropriate for the agency’s use.”
Third party websites listed inside Healthcare.gov include: Stuffit. Stuffit hosted by Smith Micro, Microsoft’s Windows including Microsoft Hotmail, Skydrive, Microsoft account, Windows live Messenger, Windows photo gallery, windows movie maker, Microsoft mail desktop, windows live writer, Bing, MSN, office.com and any other software, website or service that links to this agreement.” And others.
Here is example of what the Third Party websites, state:
Microsoft TOS
“3.3 says Content uploaded to the services “may be use, modified, adapted, saved, reproduced, distributed and displayed to the extent necessary to protect you and to provide, protect and improve Microsoft products and services…. We may occasionally use automated means to isolate information from email, chats or photos in order to help detect and protect against spam and malware….”
Microsoft places cookies in order to recognize the Users computer when an ad is displayed on it, using the information to provide more relevant ads. Users are advised software made available to download is the copyrighted work of Microsof and/or its supplies
5.2 Privacy states “You consent and agree that Microsoft may access, disclose or preserve information associated with your use of the services including (without limitation) your personal information and content or information that Microsoft acquires about you through your use of the services…”
10.5 violates Americans rights to Due Process binding them to Arbitration any portion of the Site or an, in the state of Washington, and waiving Class Action if the User lives in the United States. #18 states Microsoft may assign and transfer the agreement in any part without notice to the User.
Realnetworks.com TOS includes:
Real.com, realone, realarcade, realaudio, realvideo, realmedia, realplayer, realproducer, Helix, the Helix Design, DNA, Surestream, realplayer cloud, turboplay, perfectplay, listen.com and the real bubble
Adobe.com’s Adobe Reader has its own TOS.
Greg Roelof and Info-zip.org’s unzip extraction utility have their own TOS too.
Apple’s TOS includes: Apple Quick Time, Apples TOS, Ter- Legal Information & Notices, forbids use of “deep-link”, “page-scrape”, “robot”, “spider” or other automatic device, program, algorithm or methodology or equivalent m annual process, to access, acquire, copy or monitor any portion of the Site or any Content….Apple reserves the right to bar any such activity”
Stuffit’s TOS warns Users: those who choose to access the site do so on their own initiative and at their own risk and are responsible for complying with all local laws, rules and regulations. Smith Micro “may limit the Site’s availability in whole or in part to any person geographic area or jurisdiction we chose, at any time and in our sole discretion.” Stuffit advises the unwitting User “you agree that if any information you provide is content Microsoft takes steps to help preserve your privacy.”
Conversations addressing Internet Users being sued for Unauthorized Use of a Patent, Trademark and/or Copyright are going on- in print, online, in Broadcasts just not in relevant Congressional Hearing Rooms where witnesses called to testify are being asked what went wrong with the rollout of the Affordable Care Act. The question witnesses are not being asked is ‘what went right with the ACA roll out.’
A lot.
Healthcare.gov, the insurance marketplace and Cuidadosesalud.gov, the Spanish health site, are gravy train presenting hidden risk to the site Users, presenting great profit opportunities. Despite news cycles dominated with talk of data capture by the NSA or Consumer Data sold for mobile marketing algorithm development, there is virtually no discussion Healthcare.gov succeeded from its first click without even making one User Insurance policy sale. Healthcare.gov was brilliantly set up for profit .
Its called the business of CLICK. Lead generators and list brokers, in the financial services industry, take in $100 million a year, with their market growing by more than 16 percent annually. Within seconds of ‘landing’ on the Healthcare.gov site, even before they clicked one of the three option buttons top of the site (i) See Plans Before Apply (ii) Apply now for Health Coverage and (iii) Use Your Coverage, visitors are Bought & Sold through Online data auctions wars driven by Robots “Flash bidding” for rights to buy/sell their Identities, for Pop up placements, for sending the Visitor similar product pitches.
Healthcare.gov can be called a “List Broker.” The site has data to sell. Yours.
Take the example of John and Jane Doe and Healthcare.gov . John and Jane Doe fill out their ACA application or leave their email address or “save.” The information John and Jane Doe enter is “tested” against databases of e-mail and home addresses the lead generator already had compiled or bought. Tested is another word for background check using data you did not know the profiteers had compiled. John and Jane Doe’s entered data is being checked, keystroke by keystroke, for authenticity. Once, authenticated, John and Jane Doe’s name and data is flowed into the electronic auction system, “Ping Tree.” Data Buyers have seconds to decide to buy or pass.
The FTC knows about lead generators and list brokers. The FTC, addressing one of these entities at a time, is playing whack-a-mole. The FTC is yet to address shuttering the “model” rather than the individual players. It doesn’t take long before other such sites are put together, taking data gleaned from other sites. Spokeo. Yatedo. 123people.com are on the FTC’s radar now.
Healthcare.gov was modeled for profits not consumers. Similar models that require less personal information to be able to give Consumers “Click-to-Brick-lead,” are the online car insurance industry and other insurance models where minimal Consumer’s personal data is requested.
The Healthcare.gov online Marketplace model is similar to brick-and-mortar payday lender models, except, payday loans are typically secured by a post-dated check. Visitors must provide data on household members and income in order to price shop in the Marketplace. Income data needed to factor MAGI, Modified Adjusted Gross Income, includes, “SSI payments, disability payments, unemployment compensation, wages, salaries, tips, pension income, rental income, investment income, retirement income, prizes, awards and gambling winnings. Child support, gifts SSI, veterans disability payments, workmen’s comp and loan proceeds.”
The “future” of using this model is clear. Consumers using the Financial Industry’s parallel model have complained to Regulators their financial data has been misused or stolen after entering the auction system. The auction system is step one in Data Brokering. The FTC can testify on what the Regulators learned while investigating AMG Service Inc, an Oklahoma tribal entity selling PayDay borrowers data. The FTC learned, while investigating AMG Services In, an Oklahoma tribal entity, that once the User gave their private details, Users accounts can be entered into and withdrawn from without the User’s agreement or knowledge. AMG Services In, an Oklahoma tribal entity was selling PayDay borrowers data.
Senator Jeff Merkley, (D- Oregon) announced he is preparing a bill to outlaw online lead generation. Merkley signed on to the Affordable Health Care Act, including a provision in the 2010 health care reform law ensuring new mothers have “time and space to pump milk at work.” Merkley’s bio says nothing of protecting these moms from List Brokers and Lead Generators. [http://www.merkley.senate.gov/about/biography/ ]
Who are these List Brokers and Lead Generators benefiting from Users being Cookied, Cached, followed and auctioned without even leaving the landing page? Senator Merkley said the Financial Services Industry websites mask the true identities. Merkley has been silent on saying Healthcare.gov unmasks them.
What is known, is “the HHS Office of General Council (OGC) has determined that tools “acceptable for use without an HHS TOS agreement.” This is stated on the Healthcare.gov pages. The provided list of tools includes, but is not limited to STCI, Vencorps, Storify, Stumbleupon, Survey Monkey, Tumblr, Twitter, User Voice, Vine, Wikispaces, wordpress, xtranormal, youtube, flickr, github, google+, google moderator, google visualization, google webmaster tools, govloop, hulu, ideascale, instagram, intensedebate, linkedin, meetup everywhere, mendeley, mixedink, myspace, pinterest (photo sharing), quora, scribd.com, slidehsare, socialoomph, socialtext
Twitter is Asterisked. Measured Voice is asterisked, My.comMetrics is asterisked.
Data bundling is big business, so big that Menlo California Venture Capitol companies like Menlo Ventures [www.menloventures.com ] continue to seed companies with millions of dollars, through various rounds of funding. Some companies “make it.” Others? Well, it’s a numbers game. Seed fast, often and hope big.
An example of a Data company counting Clicks Data is LOOKSMART Ltd formerly LOOKSMART Holdings Ltd, a Delaware haven state corporation, founded in 1996 in California, #CA1991955. LOOKSmart [ www.looksmart.com ] is just being used as an example of a “Search and display advertising network solution on multiple continents. There is no known connection to the Affordable Health Care Act and Healthcare.gov, at this time, other than blood. Paul Pelosi Jr, an executive of LOOKSmart, according to Businessweek, is the son of former Speaker of the House Nancy Pelosi. Looksmart, based in California, trades on the NASDAQ under the symbol LOOK. In 2012, LOOK’s operations expense was $6 million in the year ending December 2012. LOOKSMART was delisted June 2013. It was trading at 0.76. LOOK trading January 31 2014 at $2.52 - $2.65.
That would be up to Congressional investigators to look in to and determine if and who is profiting from flash auctions, clicks, webcrawlers, list brokering, lead generating and Spam. LOOKSmart is of that genre profiting from sites like Healthcare.gov LOOKSmart does Search Advertising.
LOOKsmart uses its “Adcenter platform technology.” LOOKSmart “provides advertisers the ability to buy graphical display advertising.” “It allows multiple search advertising customers to upload keywords, manage daily budgets….” Etc, and the companies customers include “intermediaries who purchase clicks to sell into the affiliate networks of search engine providers, direct advertisers and their agencies whose objective is to obtain conversions or sales from the clicks and self service advertisers that sing up online and pay by credit cards….”
Like the ACA.
Pelosi Jr. Paul’s knowledge of this industry makes Paul a credible witness to explain to Congress exactly how the business of CLICK works and its impact on Healthcare.gov. Investing/Businessweek profiled LOOKSmart in detail [ http://investing.businessweek.com/research/stocks/snapshot/snapshot.asp?ticker=LOOK ]. “Company Description” states “The company derives the majority of its traffic from its pay-per-click distribution network partners. Each click is verified through its proprietary network traffic monitoring and management process, as well as third party technologies and tools.” It continues “Through a web interface or its proprietary API, the company’s AdCenter allows multiple search advertising customers to upload keywords, manage daily budgets, set rates and view reports, including spending data that is updated hourly. Search advertising customers can also access keyword suggestions, price and traffic estimates, online help and frequently asked questions.” It goes on to explain how AdCenters for Publishers…”integrates dominant third-party feeds, within a single auction based platform for cost-per-click text based advertising and access to a “backfill” of adverisiers so they can ramp their online operations and not lose time or existing revenue sources while establishing their advertiser relationships.”
Concerns for Healthcare.gov Users, doesn’t end there with CLICK worries. It continues. Keyword, “Sources.” Who are they?
The role of Legislators, separated by walks across the Capitol, or an amble around the corner and down the hall, is to get these questions answered. Sometimes that short distance to answers seems almost a plane ride distance cross country away. A couple of hearing rooms away from the Energy and Commerce Committee adressing oversight Of Healthcare.gov with Secretary Sebilius, the Committee on the Judiciary held an Intellectual Property hearing that should send chills up the spine of the Legislators. And Healthcare.gov Users.
This Hearing, adressing Patent Trolls, hear testimony from the Hotelier industry’s General Counsel. The General Counsel testified his Hoteliers constituency are learning the hard lesson of installing onsite WI-FI for keeping their customers’ wired. He said his Hoteliers are being sued for patent infringement by owners whose components areintegrated in to the Technology Tangle that makes WI-FI work. A spokesperson for Wendy’s explained the Internet Of Things is perceived as a “need” in a data driven make-the-consumer-happy culture. Sell through doesn’t necessarily match the expense and cost of maintenance. This isn’t guesswork. The numbers supporting evidence of trending away from IOT, should have factored in to building healthcare.gov.
Maybe it was. Click. Caching. Users are human. Curious. Crave interaction. Believe it or not, all things done, people prefer people in the flesh.
The Judiciary hearing did not bring home the lesson that (i) people don’t read to the bottom of pages where TOS and PRIVACY Clicks are positioned. Websites are tangled Technologies with multiple layers of Terms of Service and Privacy Agreements. Few of these Agreements are seen, let alone read. Fewer of the Terms Of Service are understood by site Users. The Technologies are owned by parties who are proprietary when it comes to Unauthorized use of the IP, Intellectual Property.
Even if someone did read to the page bottom, the likelihood they will read each of the CLICKS from entry to exit, is minimal. If they did? The likelihood they comprehended the ramifications of each Software’s Liabilities on the webpage, is doubtful. These Third Party sites are not bound to the Obama Administration’s “Plain Writing Act.” They should be. TOS stating the legalities Users are written in thousands of words by lawyers, are bound to, but only AFTER, John and Jane Doe hit the sites landing page. There is no warning Pop-Up (they have to click off) before being bound to the site’s consequences and Terms such as being bound to resolve through arbitration, Legal Remedies with a Cap, consequences of violating the TOS and the forum for arbitration may be cross country, for example, in California, not at all close to the Users home. More important, is the TOS they read then, in the Internet world, without notice by the software or app manufacturer, may not be there tomorrow. The Internet World is fickle that way.
Multiply the time it takes to read one software developers TOS by the number of developers software Technology tangles in the Healthcare.gov site and THEN factor in the real fact the New York Times is written for 8th grade reading level, most accomplished people can’t grasp TOS, let alone the Third Party TOS for Healthcare.gov. Jeff Foxworthy has proven few of us are smarter than a 5th grader [ http://www.tvguide.com/tvshows/are-you-smarter-than-a-5th-grader/photos/286397/55291 ]
Legislators are not grasping that Healthcare.gov, managed by the U.S. Centers for Medicare & Medicaid Services. 7500 Security Boulevard, Baltimore, MD 21244, is more than a landing page. [ whois.com indicates internic.net as a related domain name for Healthcare.gov . Internic Whois.com is ICAAN based in Los Angeles, downtown, Waterfront [ http://www.whois.com/whois/internic.net ]
ACA is a website. CMS is a website. HHS is a website. They are linked to each other. They are linked to third party sites. Websites are hacked almost daily. Websites cannot be secured even the websites of the entities that developed the software that was hacked ie. 2013- Adobe Systems, 152 million; Target Corp, 70 million; 2012- Shanghai Roadway D&B, 150 million; 2011- Sony, 77 million; 2009- Heartland Tower Federal 130 million; 2007- TJX, 94 million; 1984- TRW, Sears Roebuck, 90 million.
Ben Simo, past president of the Association for Software testing, discovered Healthcare.gov vulnerabilities. Simo did not set out to discover the ACA security vulnerabilities. Simo just wanted to insure his family. Sino said the ACA site had so much “cookie” tracking data he felt the ACA’s capacity was exceeded. Simo said the email verification system could be bypassed without even accessing his email account. Simo, preferring to call himself a software tester not hacker, said he discovered the ACA site relayed personal information over the Internet without encryption.
Healthcare.gov is covered with links to other pages, sites policies, contact us, viewers, players, even to something called the Plain Writing Act [ www.plainlanguage.gov/howto/guidelines ]. The Plain Writing Act is required of Government entities and employees to write content so Users can understand. Third Party entities linked to Healthcare.gov are not held to the Plain Writing Act standard. Visitors to the site Click away not knowing they are at risk of IP, ID, Commerce Theft and Litigation theft as they travel page to page on Healthcare.gov. This must be pointed out to site Users so they act informed. Enter Healthcare.gov, intended or not, you are giving away data to strangers who can be anywhere in the world and may one day send you a letter just like the Hotelier GC testified his clients are shocked to receive- ‘You Are An Infringer. You Are Being Sued.’
The User’s Data as List Broker or Lead Generator fodder, on the ACA timeline, is not defined. All that is stated is “Healthcare.gov will keep data collected long enough to achieve the specified objective for which they were collected” in that the gathered data falls under the National Archives and Records Administration, NARA, General Records Schedule (GRS) 20-ittem IC, “Electronic Records” handled “according to the requirements of that schedule [ www.archives-gov/records-mgmt/grs20.html ] Long enough is not defined. The question is raised if the gathered data is held in any way by National Archives and Records Administration, NARA.
Page 5 of the printed Privacy Policy advises “how healthcare.gov uses third party websites and applications,” it says, “as a response to OMB Memo M-10-06, Open Government Directive,” using a “variety of technologies and social media services to communicate and interact with citizens… third-party website and application (TPWA) tools” including “popular social networking and media sites, open source software communities and more,” without listing “more.” Examples are given- Facebook, Twitter and youtube. If reading “open source software communities” wasn’t enough to know someone, somewhere potentially knew how to enter the site or had developed a backdoor to the date, then Users, if they read this far, are advised that the “TPWAs are not exclusively operated or controlled by HealthCare.gov. Users of TPWAs often share information with the general pubic, user community and/or the third party operating the website.” “These actors may use this information in a variety of ways.” “TPWAs could cause PII to become available or accessible to healthcare.gov and the public, regardless of whether the information is explicitly asked for or collected by us.”
PII? Personally Identifiable Information.
That the Affordable Care Act, HHS and/or Healthcare.gov may have their agreement to use these Technologies does not mean visitors to ACA are grandfathered in under their agreement. Bluntly, if, as the hoteliers using WI-FI are finding out, is the day one of the Healthcare.gov’s software’s developers determines their IT IP is being used by one or many Users without legal Authority, there is the potential for each and every of the ACA Users to be sued.
Hair brained notion? Not at all.
And if John and Jane Doe decide to post their horrible experience online, their fate may be the same as Jen Palmer who wrote a negative review on Ripoff Report. Jen had not seen, in using a site she ordered product from that she never received, she had in fact agreed, ““this sales contract prohibits you from taking any action that negatively impacts KlearGear.com, its reputation, products, services, management or employees. Should you violate this clause, as determined by Kleargear.com in its sole discretion you will be provided a seventy-two(72) hour opportunity to retract the content in question. If the content remains, in whole or in part, you will be billed $3,500 USD for legal fees and court costs until such complete costs are determined in litigation. Should these charges remain unpaid for 30 calendar days from the billing date, your unpaid invoice will be forwarded to our third party collection firm and will be reported to consumer credit agencies until paid.” The unexpected $3500 bill woke Jen up.
What recourse does Healthcare.gov Users have being groomed and led in to these potential legal risks without advance notice before hitting the site’s landing page?
There are sites Users can go to to “opt out from Online Behaviour of Advertising. Aboutads.com, for one browser, indicated over 118 Participating Companies [ www.aboutads.com ] A note down the Aboutads.com page is important to read. It states “important things to remember about the choices you make on this page: These opt outs apply to interest based advertising by participating companies. You will still receive other types of online advertising from participating companies and the Web sites you visit may still collect information for other purposes.” Among the companies, Google Inc, LiveRamp, LiveRail, exelate, Glam Media and Experian Marketing Services.
HHS.gov presents an empathetic shoulder to its Users. [ Protecting the Public’s Privacy ] “Federal agencies are required to take specific steps to protect individual privacy whenever they use third-party websites and applications to engage with the public. When using a third-party website or application, agencies should adhere to the following requirements: Examine the third party’s privacy policy to evaluate the risks and determine whether the website or application is appropriate for the agency’s use.”
Third party websites listed inside Healthcare.gov include: Stuffit. Stuffit hosted by Smith Micro, Microsoft’s Windows including Microsoft Hotmail, Skydrive, Microsoft account, Windows live Messenger, Windows photo gallery, windows movie maker, Microsoft mail desktop, windows live writer, Bing, MSN, office.com and any other software, website or service that links to this agreement.” And others.
Here is example of what the Third Party websites, state:
Microsoft TOS
“3.3 says Content uploaded to the services “may be use, modified, adapted, saved, reproduced, distributed and displayed to the extent necessary to protect you and to provide, protect and improve Microsoft products and services…. We may occasionally use automated means to isolate information from email, chats or photos in order to help detect and protect against spam and malware….”
Microsoft places cookies in order to recognize the Users computer when an ad is displayed on it, using the information to provide more relevant ads. Users are advised software made available to download is the copyrighted work of Microsof and/or its supplies
5.2 Privacy states “You consent and agree that Microsoft may access, disclose or preserve information associated with your use of the services including (without limitation) your personal information and content or information that Microsoft acquires about you through your use of the services…”
10.5 violates Americans rights to Due Process binding them to Arbitration any portion of the Site or an, in the state of Washington, and waiving Class Action if the User lives in the United States. #18 states Microsoft may assign and transfer the agreement in any part without notice to the User.
Realnetworks.com TOS includes:
Real.com, realone, realarcade, realaudio, realvideo, realmedia, realplayer, realproducer, Helix, the Helix Design, DNA, Surestream, realplayer cloud, turboplay, perfectplay, listen.com and the real bubble
Adobe.com’s Adobe Reader has its own TOS.
Greg Roelof and Info-zip.org’s unzip extraction utility have their own TOS too.
Apple’s TOS includes: Apple Quick Time, Apples TOS, Ter- Legal Information & Notices, forbids use of “deep-link”, “page-scrape”, “robot”, “spider” or other automatic device, program, algorithm or methodology or equivalent m annual process, to access, acquire, copy or monitor any portion of the Site or any Content….Apple reserves the right to bar any such activity”
Stuffit’s TOS warns Users: those who choose to access the site do so on their own initiative and at their own risk and are responsible for complying with all local laws, rules and regulations. Smith Micro “may limit the Site’s availability in whole or in part to any person geographic area or jurisdiction we chose, at any time and in our sole discretion.” Stuffit advises the unwitting User “you agree that if any information you provide is content Microsoft takes steps to help preserve your privacy.”